Exploring Cryptographic Hash Functions in Cryptocurrency Networks
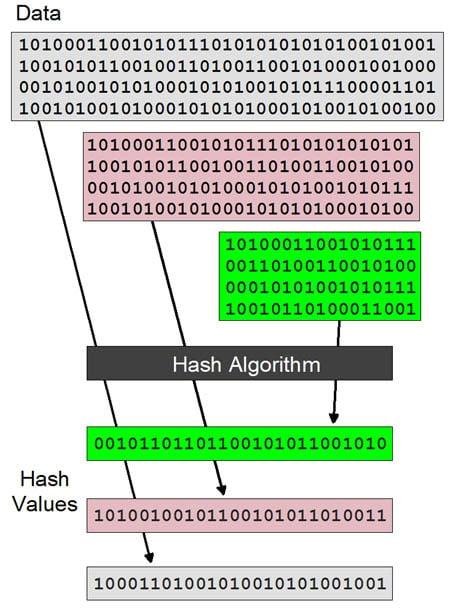
Cryptographic hash functions serve as the backbone of modern cryptocurrency networks, providing both security and integrity in the digital landscape. As decentralized systems gain traction, the need for robust mechanisms to ensure data authenticity and safeguard against malicious attacks becomes increasingly critical. This article delves into the intricate workings of cryptographic hash functions, elucidating their role in facilitating secure transactions, maintaining blockchain integrity, and enabling consensus protocols within various cryptocurrency platforms. By examining the mathematical foundations, practical applications, and potential vulnerabilities of these algorithms, we aim to enhance the understanding of their centrality in the realm of digital currencies. Through this exploration, we will illustrate how cryptographic hash functions not only underpin the trust model of cryptocurrencies but also drive innovations in blockchain technology, thereby shaping the future of digital finance.
Table of Contents
- Explaining the Role of Cryptographic Hash Functions in Ensuring Data Integrity
- Analyzing the Security Implications of Hash Function Vulnerabilities in Blockchain Technology
- Comparative Study of Popular Hash Algorithms Utilized in Cryptocurrency Networks
- Recommendations for Implementing Robust Hash Function Protocols in Crypto Applications
- In Retrospect
Explaining the Role of Cryptographic Hash Functions in Ensuring Data Integrity
Cryptographic hash functions are pivotal in maintaining the integrity of data within cryptocurrency networks. These algorithms take an input, or message, and produce a fixed-size string of characters, which appears random. Importantly, even a minor alteration in the input results in a significantly different hash output. This characteristic ensures that any changes to the data can be easily detected, keeping the integrity of the information intact. Some of the key benefits include:
- Data Verification: Each transaction is hashed, allowing users to verify its authenticity without exposing the actual data.
- Immutable Records: Once a transaction is recorded and hashed, it becomes almost impossible to alter without detection.
- Efficient Storage: Using fixed-length hashes can save space while still ensuring accuracy and reliability of data.
In cryptocurrency networks, the use of cryptographic hash functions is reflected in processes such as block creation and proof-of-work mechanisms. These functions serve as the foundation for constructing the blockchain, where each block references the hash of the previous block. This chaining secures the entire transaction history, making it computationally infeasible for any malicious actor to alter a transaction without redoing the work for all subsequent blocks. To illustrate this concept, consider the following table showcasing different hash functions utilized in cryptocurrency networks:
| Hash Function | Example Cryptocurrency | Hash Length |
|---|---|---|
| SHA-256 | Bitcoin | 256 bits |
| Keccak-256 | Ethereum | 256 bits |
| RIPEMD-160 | Bitcoin Address Generation | 160 bits |
Analyzing the Security Implications of Hash Function Vulnerabilities in Blockchain Technology
Hash functions serve as the backbone of security in blockchain networks, facilitating data integrity and authenticity. However, vulnerabilities in these cryptographic algorithms could have dire consequences for decentralized systems. The potential for pre-image and collision attacks can undermine trust within the network, as malicious actors could exploit these weaknesses to forge transactions or manipulate data. It is crucial for developers and stakeholders to be aware of the risks associated with hash function vulnerabilities, especially as consensus mechanisms rely heavily on these algorithms to validate transactions and secure blockchains.
To effectively analyze the security implications, several factors must be considered:
- Algorithm Strength: The robustness of the hash function plays a critical role in its ability to withstand attacks.
- Network Dynamics: The structure and size of the network can influence the risk level, particularly in smaller networks where a few nodes can dictate the consensus.
- Upgrade Path: The readiness of the network to implement stronger cryptographic standards is essential for long-term security.
Utilizing modern alternatives, like SHA-3 or BLAKE2, could mitigate existing vulnerabilities and ensure that as technology evolves, so do the protective measures in place. A proactive approach to maintaining hash integrity is necessary to safeguard assets and maintain decentralization.
Comparative Study of Popular Hash Algorithms Utilized in Cryptocurrency Networks
The landscape of cryptocurrency networks is significantly shaped by the hash algorithms they employ, with each algorithm bringing unique attributes that can influence network security, transaction speeds, and decentralization. Among the most prominent hash functions in use are SHA-256, used by Bitcoin, and Ethash, employed by Ethereum. SHA-256 is characterized by its robust security level, requiring substantial computational resources, making it resilient against potential attacks but also leading to higher energy consumption. On the other hand, Ethash was designed to be memory-hard, promoting a more egalitarian mining environment by enabling less powerful hardware to contribute to the process, thus enhancing accessibility and decentralization within the Ethereum ecosystem.
Comparing these hash algorithms reveals a variety of critical differences that can impact user experience and system efficiency. Some key factors to consider include:
- Security Level: The resistance to various types of attacks.
- Efficiency: Energy consumption and computational power requirements.
- Mining Accessibility: The availability of compatible hardware for mining.
| Hash Algorithm | Network | Security (Rating) | Mining Resistance |
|---|---|---|---|
| SHA-256 | Bitcoin | High | High |
| Ethash | Ethereum | Medium-High | Low |
| Blake2b | Decred | Medium-High | Medium |
This comparative analysis underscores the ongoing evolution of hash algorithms in the realm of cryptocurrency, revealing how choices made in algorithm design can steer the direction of a network’s functionality and user engagement.
Recommendations for Implementing Robust Hash Function Protocols in Crypto Applications
To ensure the integrity and security of cryptocurrency networks, it is critical to implement robust hash function protocols. Key recommendations for this process include the selection of hash functions based on their resistance to collision and preimage attacks. Prioritize established cryptographic algorithms such as SHA-256 or Keccak-256, which have undergone extensive scrutiny and peer review. Additionally, consider using adaptive hashing techniques to mitigate risks associated with brute-force attacks, especially on user-generated data.
Moreover, it is advisable to regularly review and update hash function protocols as advancements in computational power and cryptanalysis techniques emerge. This can be achieved by:
- Conducting periodic security audits of the implemented hash functions.
- Staying informed about cryptographic research and emerging standards.
- Implementing multi-layered security measures, such as salt and pepper, to enhance hash function effectiveness.
| Hash Function | Strength | Use Cases |
|---|---|---|
| SHA-256 | High | Bitcoin, Security Tokens |
| Keccak-256 | Very High | Ethereum, Smart Contracts |
| BLAKE2 | High | General Purpose, Digital Signatures |
In Retrospect
the exploration of cryptographic hash functions within cryptocurrency networks underscores their pivotal role in ensuring security, integrity, and efficiency. As the backbone of blockchain architecture, these functions not only facilitate secure transaction verification but also contribute to the consensus mechanisms that govern decentralized systems. The mathematical properties of cryptographic hash functions, including pre-image resistance, collision resistance, and deterministic output, empower developers to build trustless environments where users can engage in peer-to-peer transactions with confidence.
As the cryptocurrency landscape continues to evolve, further innovations in hash functions and cryptographic techniques will undoubtedly emerge, enhancing scalability and resilience against increasingly sophisticated attacks. For stakeholders within the industry, including developers, researchers, and investors, a nuanced understanding of these cryptographic principles is essential. Continued scholarly discourse and practical research into their applications will be critical for the advancement of secure and efficient blockchain technologies.
Ultimately, as we forge ahead in this rapidly progressing digital frontier, the significance of cryptographic hash functions cannot be overstated. Their ongoing evolution will play a crucial role in the future of secure communications and financial systems, highlighting the continuous interplay between cryptography and the growing ecosystem of cryptocurrencies.
