Exploring Proof of Authority (PoA) in Cryptocurrency Networks
Introduction
In the rapidly evolving landscape of cryptocurrency, consensus mechanisms play a pivotal role in ensuring the integrity, security, and efficiency of blockchain networks. Among the various paradigms that have emerged, Proof of Authority (PoA) stands out as a unique approach, particularly suited for private or consortium blockchains. Unlike its more decentralized counterparts, such as Proof of Work (PoW) and Proof of Stake (PoS), PoA relies on a limited number of pre-approved validators who are granted authority based on their identity and reputation rather than computational power or capital investment. This article delves into the intricacies of Proof of Authority, examining its operational framework, advantages, and challenges within cryptocurrency networks. By providing a thorough analysis of PoA’s mechanisms and its applicability in various scenarios, we aim to contribute to a deeper understanding of this consensus model and its potential impact on the future of blockchain technology.
Table of Contents
- Understanding the Mechanisms of Proof of Authority in Blockchain Frameworks
- Evaluating the Security Implications of PoA in Cryptocurrency Networks
- Optimizing Network Efficiency through PoA Consensus Models
- Best Practices for Implementing Proof of Authority in Decentralized Applications
- To Wrap It Up
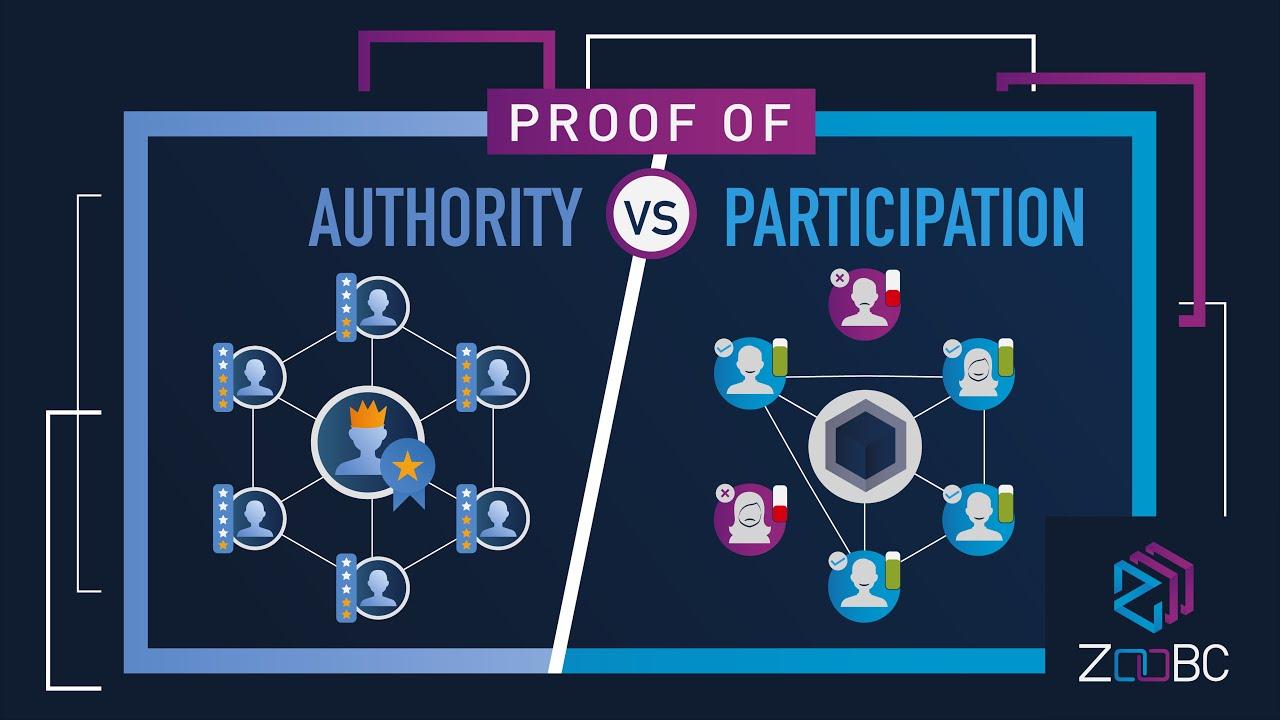
Understanding the Mechanisms of Proof of Authority in Blockchain Frameworks
Proof of Authority (PoA) stands out in blockchain frameworks as a unique consensus mechanism that prioritizes identity and reputation over computational power. In PoA networks, a limited number of validators, often known for their credibility and trustworthiness, are entrusted with validating transactions. This enables faster transaction times and greater scalability compared to other consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS). The mechanism significantly reduces the resources needed for maintaining the blockchain, which can lead to lower operational costs and environmental impact.
Key features of Proof of Authority include:
- Identity-based Validation: Validators are pre-approved based on their reputation, which minimizes the likelihood of malicious activity.
- Efficiency: The centralized nature of authority enables quicker transaction confirmations and high throughput.
- Lower Entry Barriers: PoA frameworks can facilitate new projects and enterprises that may lack the technical expertise or resources to engage in traditional consensus models.
| Feature | Description |
|---|---|
| Speed | High transaction speeds due to limited validator participation. |
| Scalability | Impressive scalability that can support numerous transactions without significant lag. |
| Security | Focus on trusted nodes ensures a secure environment against attacks. |
Evaluating the Security Implications of PoA in Cryptocurrency Networks
The Proof of Authority (PoA) consensus mechanism operates on the foundation of trusted validators, often leading to criticisms surrounding its security architecture. Unlike its permissionless counterparts, PoA networks rely on a select group of nodes that are pre-approved to validate transactions and create new blocks. This centralization, while enhancing efficiency and speed, can become a target for various attacks. Potential security vulnerabilities in PoA networks include:
- Node Compromise: If a validator’s private key is compromised, an attacker could manipulate transaction validation.
- Sybil Attacks: Although minimized by identity verification, attackers could potentially create multiple false identities to disrupt consensus.
- Collusion Risks: A small number of validators can collude to alter the state of the blockchain for malicious purposes.
The security implications further extend to regulatory concerns, particularly in environments requiring compliance with legal frameworks. As PoA networks typically involve identifiable validators, they may incur stricter regulatory scrutiny, affecting user privacy and operational autonomy. To illustrate the implications, consider the following comparison of PoA to other consensus mechanisms:
| Aspect | Proof of Authority | Proof of Work |
|---|---|---|
| Decentralization | Low | High |
| Transaction Speed | High | Low |
| Electricity Consumption | Low | High |
| Security Risks | Centralized threats | 51% attacks |
Ultimately, while PoA offers several advantages in terms of transaction efficiency and speed, its security implications necessitate a thorough evaluation to ensure that the benefits do not come at an unacceptable cost to network integrity and user trust.
Optimizing Network Efficiency through PoA Consensus Models
Proof of Authority (PoA) consensus models are gaining traction in cryptocurrency networks due to their ability to significantly enhance network efficiency. By validating transactions through a limited number of approved nodes, PoA reduces the computational overhead and time delays associated with traditional consensus mechanisms like Proof of Work (PoW). This streamlined approach allows for faster transaction processing and an overall increase in throughput, making PoA particularly suited for applications requiring speed and scalability. Some key features contributing to network efficiency include:
- Fast Finality: Transactions are confirmed almost instantaneously, providing immediate assurance.
- Low Power Consumption: PoA minimizes the need for extensive computational power, leading to reduced energy costs.
- Increased Security: With a limited number of validators, the risk of attack is mitigated as long as the validators are trustworthy.
To illustrate the advantages of PoA in optimizing network efficiency, consider the comparison of transaction speeds among different consensus mechanisms. The table below provides insights into the average transaction confirmation times, showcasing how PoA stands out:
| Consensus Mechanism | Average Transaction Confirmation Time (Seconds) |
|---|---|
| Proof of Work | 10+ |
| Proof of Stake | 6-30 |
| Proof of Authority | 1-3 |
These metrics highlight the superior speed and efficiency of PoA over its PoW and PoS counterparts, making it a preferred choice for businesses looking to leverage blockchain technology while ensuring rapid transaction processing. As the landscape of cryptocurrency evolves, embracing PoA could be pivotal for organizations aiming to optimize performance in their operations.
Best Practices for Implementing Proof of Authority in Decentralized Applications
When implementing Proof of Authority in decentralized applications, it is crucial to establish a robust governance framework. This involves clearly defining the roles and responsibilities of validators within the network. Emphasizing transparency and accountability helps to mitigate risks associated with centralized control. Key practices to consider include:
- Validator Selection: Opt for validators with a proven track record and relevant expertise.
- Performance Monitoring: Continuously evaluate validators’ performance to ensure they meet the network’s standards.
- Audit Mechanisms: Implement regular audits to assess compliance with the established governance criteria.
Moreover, ensuring effective communication among stakeholders is vital for fostering trust and engagement within the community. Utilizing decentralized channels for information dissemination can enhance participation and feedback. Some additional best practices are:
- Community Engagement: Facilitate discussions and forums to gather input from users and validators alike.
- Documentation: Maintain comprehensive documentation for protocols and updates to establish clear guidelines.
- Dispute Resolution: Develop a structured process for addressing conflicts among validators or users to uphold fairness.
To Wrap It Up
Proof of Authority (PoA) represents a significant evolution in the consensus mechanisms used within cryptocurrency networks. By prioritizing identity and reputation over energy-intensive computations or vast decentralized validation, PoA establishes a streamlined and efficient framework conducive to various applications, particularly in environments where trust and speed are paramount.
As we continue to navigate the complexities of blockchain technology, the adoption of consensus models like PoA will likely expand, paving the way for innovative solutions tailored to specific use cases. However, it is essential to remain vigilant regarding the inherent trade-offs of centralized authority within decentralized systems. Ongoing research and dialogue within the community will be crucial to address concerns surrounding centralization, security, and potential vulnerabilities.
The future of PoA holds promise, but it also demands a critical assessment of its implications on the broader ecosystem and its role in shaping the next generation of blockchain applications. As developers, stakeholders, and researchers push forward, maintaining a balanced perspective on governance, scalability, and trust will define the landscape of PoA and its impact on the evolving cryptocurrency paradigm.