Advanced Cryptography Techniques for Securing Cryptocurrency Transactions
In the rapidly evolving landscape of digital finance, the security of cryptocurrency transactions has become a paramount concern for both users and developers alike. As the adoption of blockchain technology continues to accelerate, so too does the sophistication of cyber threats targeting these decentralized systems. Consequently, advanced cryptography techniques have emerged as critical tools in the safeguarding of cryptocurrency assets, enabling secure and tamper-resistant transactions. This article delves into the latest innovations in cryptographic methods, such as zero-knowledge proofs, homomorphic encryption, and post-quantum cryptography, highlighting their applications in enhancing transaction privacy, integrity, and resilience against emerging security threats. By examining these advanced techniques, we aim to provide a comprehensive overview of how cryptography is shaping the security landscape of digital currencies, ensuring that users can transact with confidence in an increasingly interconnected world.
Table of Contents
- Exploring the Role of Zero-Knowledge Proofs in Enhancing Privacy for Cryptocurrency Transactions
- Implementing Homomorphic Encryption for Secure Transaction Processing and Data Privacy
- Utilizing Multi-Signature Schemes to Strengthen Accountability and Asset Protection in Cryptocurrencies
- Adopting Post-Quantum Cryptography to Future-Proof Financial Assets Against Emerging Threats
- Final Thoughts
Exploring the Role of Zero-Knowledge Proofs in Enhancing Privacy for Cryptocurrency Transactions
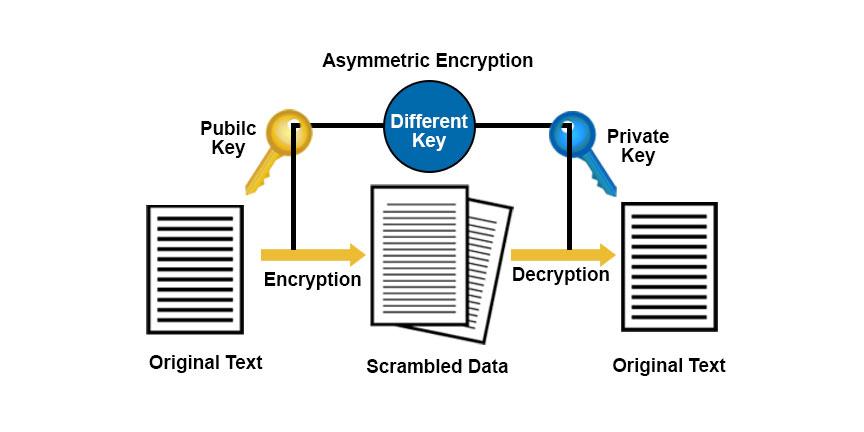
Zero-knowledge proofs (ZKPs) are a groundbreaking cryptographic method that enables one party to prove to another that a statement is true without revealing any specific information about the statement itself. This property is crucial in the context of cryptocurrency transactions, where privacy and confidentiality are paramount. ZKPs ensure that transaction details remain hidden while still authenticating the validity of the transaction, thereby enhancing user trust and protecting sensitive financial information. By employing ZKPs, cryptocurrency projects can mitigate various security risks associated with revealing transaction history or wallet balances.
In practice, implementing zero-knowledge proofs can take several forms, with notable methods such as zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) and zk-STARKs (Zero-Knowledge Scalable Transparent Arguments of Knowledge). Each method offers distinct advantages in terms of efficiency and security. For instance, while zk-SNARKs are typically faster and require less data, they involve a trusted setup phase, whereas zk-STARKs provide a trustless framework at the cost of increased computational resources. The adoption of these technologies within cryptocurrency networks is paving the way for a more secure and private future, allowing users to engage in transactions with reduced risk of exposure to malicious actors.
Implementing Homomorphic Encryption for Secure Transaction Processing and Data Privacy
Homomorphic encryption is an advanced cryptographic technique that allows computations to be performed on encrypted data without requiring decryption. This characteristic is particularly beneficial for enhancing security in cryptocurrency transactions, as it enables users to conduct secure operations such as transfers, querying balances, and executing contracts without exposing sensitive information. By leveraging this technology, financial institutions and cryptocurrency platforms can ensure that personal and transaction data remain confidential, thereby fostering trust between users and service providers. Some key advantages of homomorphic encryption include:
- Data Security: Protects user information even while processing transactions.
- Compliance: Helps organizations meet regulatory requirements for data protection.
- Scalability: Supports a variety of operations on encrypted data, accommodating growing transaction volumes.
Implementing homomorphic encryption in transaction processing architectures does come with challenges, mainly related to performance and complexity. Encrypted computations can be significantly slower than their plaintext counterparts, necessitating optimizations to maintain user experience. Moreover, the integration of homomorphic encryption requires thorough understanding and skilled personnel to manage the intricacies involved. To provide a clearer understanding of how this technique can be incorporated into existing systems, consider the following aspects that need to be addressed:
| Aspect | Considerations |
|---|---|
| Performance Optimization | Utilize advanced algorithms and hardware acceleration. |
| System Compatibility | Ensure encryption methods integrate seamlessly with existing infrastructures. |
| Cost Implications | Evaluate the expense of implementing specialized technologies versus potential benefits. |
Utilizing Multi-Signature Schemes to Strengthen Accountability and Asset Protection in Cryptocurrencies
Multi-signature schemes are an innovative approach that enhances both accountability and asset protection in the realm of cryptocurrencies. By requiring multiple private keys to authorize a transaction, these mechanisms significantly reduce the risk of unauthorized access and theft. Unlike traditional single-key wallets, multi-signature accounts can be configured to require a specific number of signatures from different parties—this ensures that no single individual holds full control over the funds. The configurability of these schemes allows for various arrangements, such as requiring signatures from a board of directors or a family group, promoting transparency and shared responsibility.
Implementing such schemes can bring several advantages to users and organizations alike. For instance, they can help mitigate risks associated with lost or compromised keys and can serve as a deterrent against fraud and mismanagement. Here are a few key benefits of employing multi-signature arrangements:
- Enhanced Security: Reduces the likelihood of theft by requiring consensus before fund access.
- Improved Control: Distributes power among multiple stakeholders, reinforcing checks and balances.
- Convenience: Allows for flexible configurations to suit the specific needs of an organization or individual.
- Dispute Resolution: In cases of disagreement, transactions can be halted until a majority resolution is achieved.
Adopting Post-Quantum Cryptography to Future-Proof Financial Assets Against Emerging Threats
As quantum computing continues to advance, the financial sector must prepare for a potential upheaval in security protocols. Traditional cryptographic systems, such as RSA and ECC, could become vulnerable to quantum attacks, enabling attackers to compromise sensitive financial assets within moments. This scenario necessitates the adoption of post-quantum cryptography, which incorporates algorithms specifically designed to resist the computational power of quantum machines. By implementing these new cryptographic frameworks, financial institutions can significantly enhance the security of cryptocurrency transactions, safeguarding investors’ assets from the repercussions of emerging threats.
The transition to post-quantum solutions encompasses various methodologies, each offering unique advantages. Consider the following key attributes when selecting suitable post-quantum algorithms:
- Resistance to Quantum Attacks: The primary focus should be on algorithms that can withstand attacks from quantum computers.
- Efficiency: Solutions must maintain performance efficiency to ensure seamless transactions without excessive overhead.
- Standardization: Support from recognized bodies, such as NIST, is crucial to ensure the algorithms are viable and widely accepted.
| Algorithm Type | Security Level | Implementation Status |
|---|---|---|
| Lattice-Based | High | Under active research |
| Code-Based | Moderate | Implementation available |
| Hash-Based | High | Standardized |
As we look towards a future where quantum threats may become ubiquitous, prioritizing the integration of these post-quantum algorithms into financial systems will be essential. Collaborating among stakeholders, including cryptographers, developers, and regulators, will pave the way for robust security models that ensure the integrity and trustworthiness of cryptocurrency transactions.
Final Thoughts
the evolution of cryptocurrency necessitates the integration of advanced cryptographic techniques to enhance the security and integrity of transactions. As digital currencies continue to gain traction in global financial systems, the adoption of sophisticated methodologies such as zero-knowledge proofs, multi-signature schemes, and homomorphic encryption is imperative for addressing the ever-present vulnerabilities that accompany decentralized networks.
These advanced strategies not only bolster user confidence but also lay the groundwork for future innovations in blockchain technology. By deploying stronger cryptographic frameworks, stakeholders can mitigate risks associated with fraud, enhancing the resilience of cryptocurrency systems against potential threats.
As we move forward, ongoing research and development in cryptography will be crucial in navigating the balance between privacy, scalability, and security. It is vital for developers, regulators, and users to stay abreast of these advancements, fostering a collaborative approach to create a secure and robust digital currency ecosystem that stands the test of time. In this rapidly evolving landscape, those who invest in understanding and implementing these techniques will be better positioned to leverage the transformative power of cryptocurrencies while safeguarding against emerging risks.